Cloud Penetration Test Report

Executive Summary
From June 12th to July 10th, 2024, SS Pentesting conducted a cloud penetration test for Example Corporation to assess its cloud security. The assessment identified multiple critical vulnerabilities, including credentials exposed in the website’s source code (Finding INT-001). This led to initial access into the cloud environment where it was later discovered that sensitive data was exposed in plain text. This is to include credit card information (Finding INT-002), access tokens (Finding INT-006), and credentials stored in Runbooks (Finding INT-005). Additionally, it was discovered that several users were using weak passwords (Finding INT-004), increasing the risk of lateral movement and potential privilege escalation. This report provides a high-level overview of these findings, their impact, and remediation strategies. For further details, refer to the Technical Findings section.
Confidentiality Statement
This document is the exclusive property of Example Corporation. This document contains proprietary and confidential information. Duplication, redistribution, or use, in whole or in part, in any form, requires consent of Example Corporation or SS Pentesting. Example Corporation may share this document with auditors under non-disclosure agreements to demonstrate penetration test requirement compliance.
Disclaimer
A penetration test is considered a snapshot in time. The findings and recommendations reflect the information gathered during the assessment and not any changes or modifications made outside of that period. Time-limited engagements do not allow for a full evaluation of all security controls. SS Pentesting prioritized the assessment to identify the weakest security controls an attacker would exploit. SS Pentesting recommends conducting similar assessments on an annual basis by internal or third-party assessors to ensure the continued success of the controls.
Contact Information
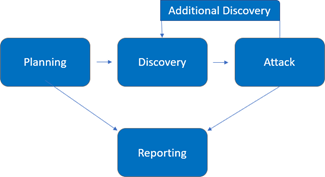
Assessment Overview
The Penetration testing process included the following phases:
- Planning – Customer goals are gathered, and rules of engagement obtained.
- Discovery – Perform scanning and enumeration to identify potential vulnerabilities, weak areas, and exploits.
- Attack – Confirm potential vulnerabilities through exploitation and perform additional discovery upon new access.
- Reporting – Document all found vulnerabilities and exploits, failed attempts, and company strengths and weaknesses.
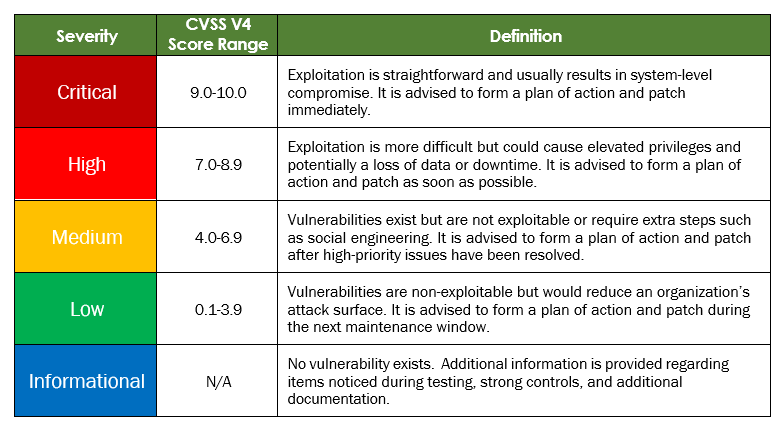
Finding Severity Ratings
The following table defines severity levels and their corresponding CVSS score ranges, which are used throughout this document. These severity levels help assess risk by evaluating the likelihood and impact of each vulnerability.
Risk Factors
Risk is measured by two factors, Likelihood and Impact:
Likelihood: Likelihood measures the potential effect of a vulnerability being exploited. Ratings are given based on the difficulty of the attack, the available tools, attacker skill level, and client environment.
Impact: Impact measures the potential vulnerability’s effect on operations, including confidentiality, integrity, and availability of client systems and/or data, reputational harm, and financial loss.
Scope
Scope Exclusions: Per client request, SS Pentesting did not perform any of the following attacks during testing:
- Denial of Service (DoS)
- Phishing/Social Engineering
All other attacks not specified above were permitted by Example Corporation.
Client Allowances:
Example Corporation provided SS Pentesting the following allowances: Authorization of tests on Example Corporation’s cloud environment.
Key Strength and Weaknesses
The following identifies a key strength found during this assessment:
- Strong logging and monitoring configurations.
The following identifies key weaknesses found during this assessment:
- Source code misconfigurations.
- Credential and key management issues.
- Data protection challenges.
Vulnerability Summary & Report Card
The following table categorizes the vulnerabilities found by severity. Remediation recommendations are also provided.
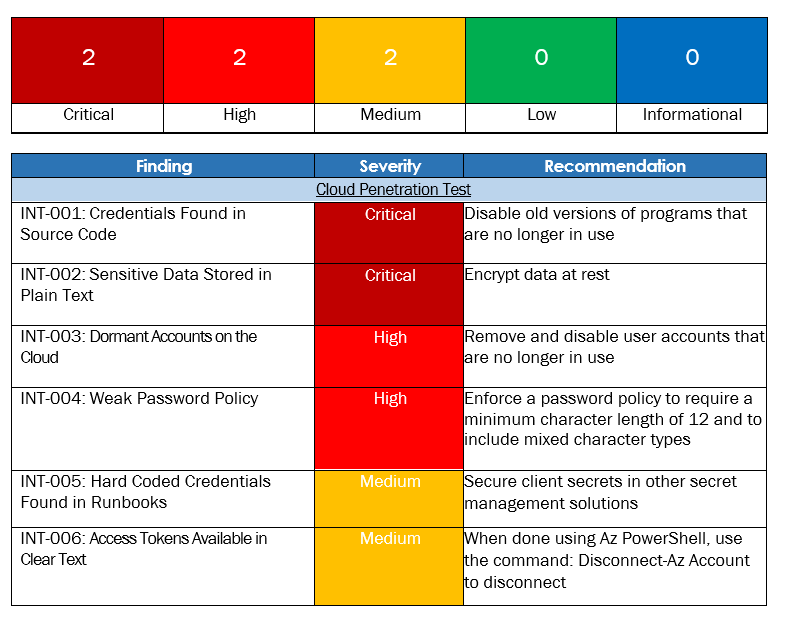
Cloud Penetration Test Findings
Finding INT-001: Credentials Found in Source Code Critical

Figure 1.1: Shows a zip file that is accessible through the source code from an old version of microsoft blobs.
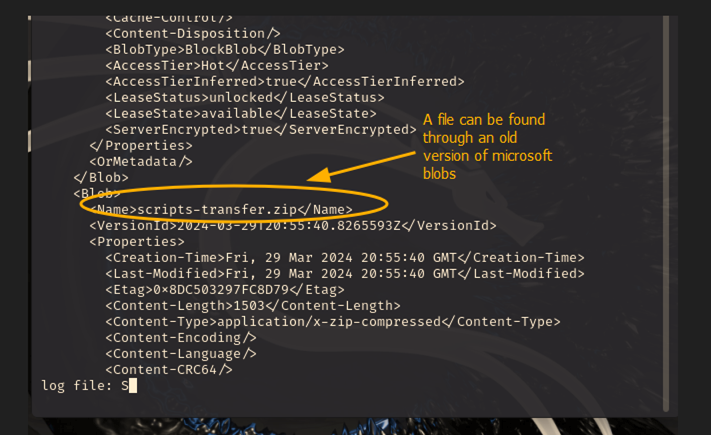
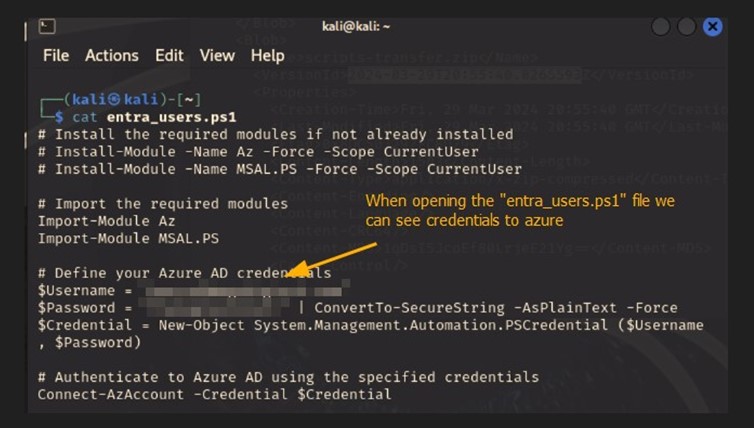
Figure 1.2: Shows credentials from unzipping the file.
Remediation: Permanently disable old versions of programs that are no longer in use.
Reference: Keep passwords out of source code - why and how
Finding INT-002: Sensitive Data Stored in Plain Text Critical
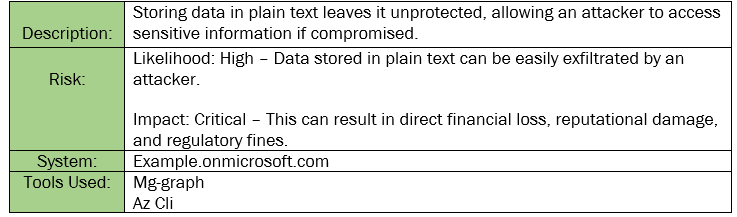
Figure 2.1: Shows a database of credit card numbers stored in plain text.
Remediation: Encrypt data at rest and enforce encryption policies for cloud storage.
Reference: Top 5 PCI DSS Encryption Requirements - Sprinto
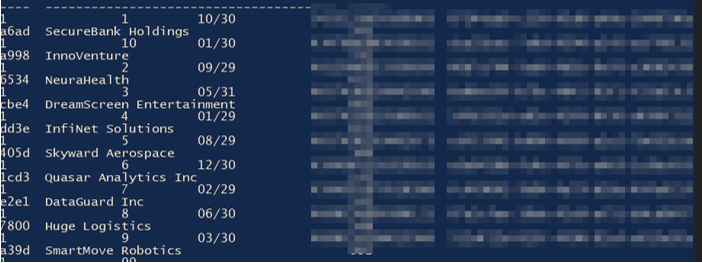
Finding INT-003: Dormant Accounts on the Cloud High
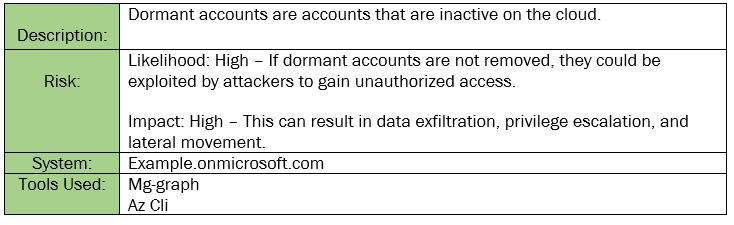
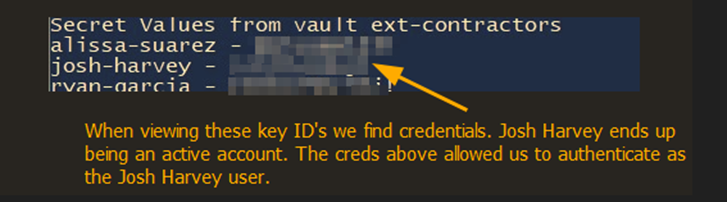
Figure 3.1: Shows secrets to various external contractors.
Remediation: Disable / de-activate accounts that are no longer in use.
Reference: Fix user creation and deletion issues in Microsoft Entra ID - Azure
Finding INT-004: Weak Password Policy High
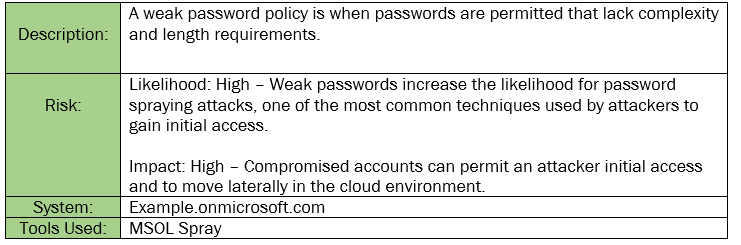
Figure 4.1: Shows a successful result from a password spray attack.
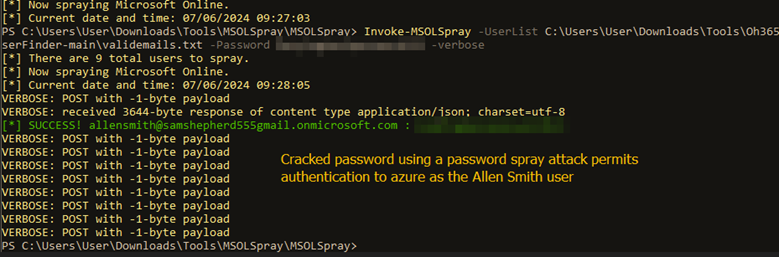
Remediation: Enforce a password policy requiring a minimum of 12 characters, including uppercase letters, lowercase letters, and special characters. Implement multi-factor authentication (MFA) to add an additional layer of security.
Reference: Create and use strong passwords - Microsoft Support
Finding INT-005: Hard-Coded Credentials Found in Runbooks Medium
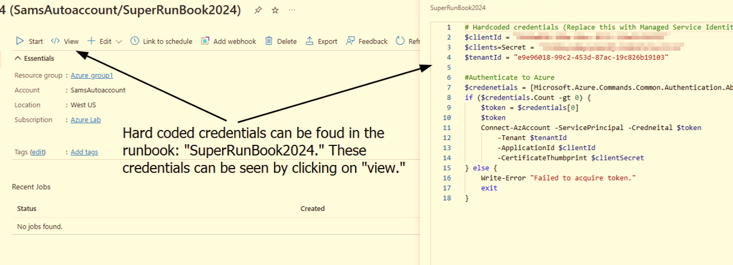
Figure 5.1: Shows client ID and a client secret available in the runbook, SuperRunBook2024.
Remediation: Store client secrets in Azure Key Vault.
Reference: How to Prevent Hardcoded Passwords? - O360
Finding INT-006: Access Tokens Available in Clear Text Medium
Figure 6.1:
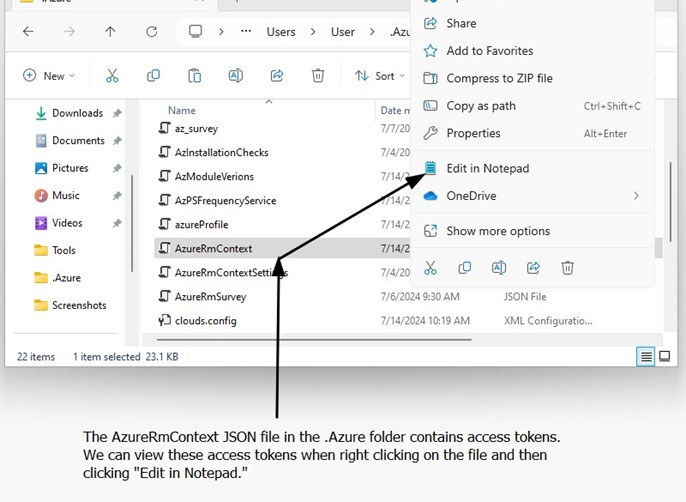
Figure 6.2:
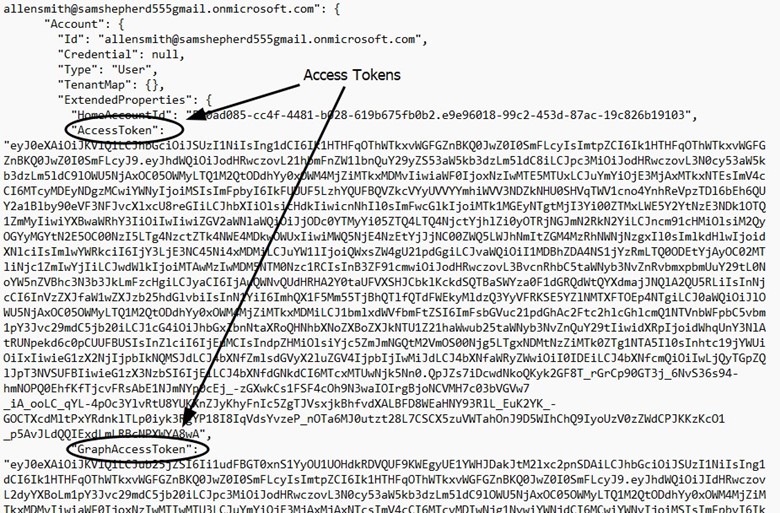
Remediation: These JSON files only exist if you have an active session. When done using Az PowerShell, use the command: Disconnect-AzAccount to disconnect. Never use the command: Save-AzContext, as this will save the session and thus the tokens in the .azure folder.
Reference: Securely Storing an Access Token - Stack Overflow
Conclusion
During testing, a recurring theme was misconfiguration of sensitive data storage. We recommend Example Corporation implement various methods to secure data which would include using encryption and implementing secret management tools.
On a positive note, Example Corporation had strong logging and monitoring configurations. We recommend that the Example Corporation team thoroughly review the recommendations made in this report, correct the findings, and re-test annually to improve their overall security posture.